Mar. 07, 2021
A Foundation for the Third Internet Era
The world wide web has 4.5 billion people in it. Yet five mega-tech corporations hold the keys to almost every interaction we make over the Internet.

Those centralized “trusted” entities have treasure troves of sensitive data containing exabytes of information that are banal to sift through for you, but are blood diamonds for computer power of the highest order with intelligent machine learning algorithms that make sense of that data. Once those gems have been processed and polished for consumption, the result of that output is ads being fed back to you—generating big ad dollars through big data, at everyone’s expense. Jeff Hammerbacher, co-founder of Cloudera, famously said, "The best minds of my generation are thinking about how to make people click ads."
Yet the Internet didn’t start out this way. It started out decentralized before the advent of the second era of the internet—of social media and user-generated content—before we turned the corner into the 2000s. It was an online world made up of usenet, RSS, and email before it was Gmail, bittorrent, and many disparate forums, each with their little niches—hidden easter eggs spread out across the many corners of Web 1.0. The Internet was a much bigger world back then with much fewer people in it.
"Services on the Internet have become more centralized beginning in the 1990s, but do not fulfill the original decentralized vision of the Internet."—Handshake whitepaper
Email became Gmail. Usenet became Reddit. Blog replies became Facebook and Medium. Pingbacks became Twitter. Squid became Cloudflare. Even Gnutella became The Pirate Bay.
Today, there are less than 10 “watering holes” where 4.5 billion people online gather. And the platforms that run those watering holes moderate just about everything that we do. All that hustle and bustle of our online lives are logged, stored, and served by them; not you. But the issue runs deeper than that—much deeper.
If we trace the chain of command up to the highest levels, it’s plain to see who ultimately holds the keys to the castle of the Internet. The answer isn’t what you might think. It doesn’t stop at Twitter, Facebook, Amazon, or even Google. Much of it stops at the US government.
Let’s use Twitter as the default example tech company for the purposes of this post. Twitter runs a subdomain on the top-level domain (TLD) “com”, which is one of two of the Internet’s most important TLDs—you might be familiar with it. It also happens to be owned and operated by the $23.66 billion dollar US company, VeriSign. VeriSign, in turn, registers .com, .net. and .org under ICANN’s authoritative root zone file—the ultimate, canonical root zone in the hierarchical namespace above which all domain names on the Internet sit below. ICANN, in turn, operates under the jurisdiction of the US government. As in, ICANN can be subjugated by US law, and in a sense, is a single point of failure.
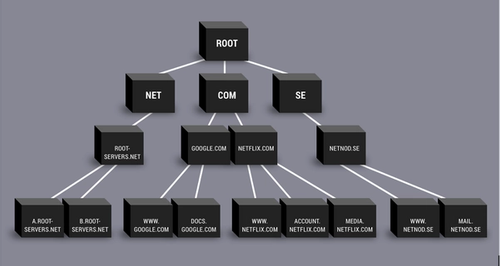
“Root” sits at the top of the hierarchical namespace. It represents the root zone file, which is simply a text file maintained by ICANN that lists ~1200 TLDs.
Most people aren't aware that the U.S Army and the Department of Defence each run a root server in traditional-DNS-land. There are a total of just 13 root servers that serve the root zone, essentially authenticating every interaction over the Internet. VeriSign runs 2 out of the 13 root servers!! ICANN runs IANA, the standards body that assigns IP addresses and manages the DNS root zones, to name a few of its functions. You can now start to see just how alarmingly centralized the Internet is for how vast it appears.
The consequences of this command-and-control structure is what we’re going to be exploring throughout this article. When you think about the Internet, you think of it as open in the "world wide web" sense, enabling communication and linkage between information. But the reality is that the system is beholden to US law—not necessarily a bad thing; it’s just not what most people who use the Internet would expect. Taken in this context, it’s less surprising that N. America's adversaries pursue their own versions of the Internet (e.g. Russia, China, and others)—because to leave it open is to leave it in control of the United States.
If, for example, you do something that is seen as problematic in the eyes of the US government, the DOJ can seize all of your online assets beginning with your domain. Seizing your domain is trivial to do because, as you’ve learned, it so happens that some of the biggest DNS servers are run by the DOJ and the US army. This is an asymmetrically low-effort, high-impact strategy because, in order for them to take down your domains, they’d just make a record change—a flip of the switch from the DOJ’s perspective—extremely trivial. They can get to your site’s domains faster than they can get to you or your financial assets. With this as a hammer, it’s easy to nail you—and anyone on the Internet for that matter—at the DNS level.
You can connect the dots from here. As blockchain-enabled financial services and decentralized finance grow, Internet participants will bump up against the limits of today's highly centralized trust models, where major web services are administered primarily by large, monopolistic for-profit corporations.
"If Bitcoin is the steel of cyber-architecture, then Domains are the real estate holdings underneath, anchoring the virtual age in the bedrock of language and providing portals to the digital networks critical to life now & yet to come."—Michael Saylor, CEO of MicroStrategy
Protocols, Not Platforms
If you haven’t already read this, I strongly recommend that you do: “Protocols, Not Platforms: A Technological Approach to Free Speech”, by Mike Masnick. In it, he argues the merits of returning to a system of complementary protocols that together can provide services on par with the kinds of services you’re used to getting from platforms served up by your familiar social networks.
Masnick: "In this article, I am proposing that we return to a world of protocols dominating the Internet, rather than platforms. There is reason to believe that moving to a system of protocols could solve many of the problems associated with platforms today and that it could be done while minimizing the problems that were inherent to protocols a few decades ago.
While there is no silver bullet, a system of protocols could serve to do a better job of protecting both user privacy and free speech, while at the same time minimizing the impact of abusive behavior online and creating new and compelling business models that are more aligned with user interests."
The Internet, as it stands, runs on a client-server, or server-based, model. A really simple illustration of it looks like the following diagram:
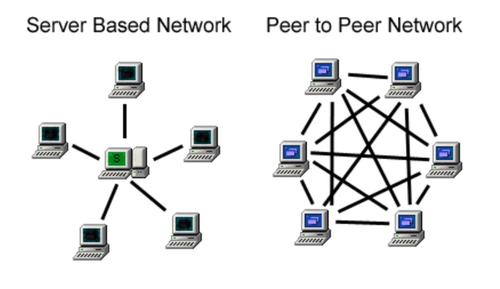
Now imagine a parallel universe where you’re on a decentralized, peer-to-peer (p2p) social network. What that experience will allow you to do is, rather than having a platform like Twitter deciding one day that your tweets can no longer be viewed by anybody else, you would instead communicate on a network that no one—and simultaneously everyone—controls. Thus a Twitter-equivalent “host” could not make decisions over the discourse—because you’re not on someone else’s private platform; you’re on an open, public peer-to-peer network—a digital agora, if you will.
For a lot of use cases, the client-server web works just fine. But for a certain subset of use cases, an alternative that is strongly decentralized from the get-go, that will allow you to literally gossip p2p, is really important. We saw the importance of this in action on many of the major events that unfolded year-to-date, most notably with the takedown of Parler.
You can start to realize the power of protocols. By leveraging peer-to-peer data sharing and storage, we can create a version of the web that makes it impossible for any centralized entity to act as the gatekeeper of online content. This web doesn’t exist in some parallel universe; it’s here now. The fully realized vision of this web will be many years in the making.
But for the first time in a long time spanning the Internet’s history, power users who can begin to take back control over the Internet and not just be relegated to the attention shafts that machine learning algorithms mine for advertisement dollars.
The first step in walking through the door begins with a name.
Why Decentralized Naming is the Next Killer App of Blockchain Technology
"Whatever we build, it must be about all of us and none of us at the same time."—author unknown
The Handshake Naming System (HNS) is a game changer the likes of which its predecessors, competitors, and future forks make (and will make) attempts at but fail to solve the problem from the root. The Handshake blockchain is simply an append-only database, where the database is a replacement of the root zone’s text file that’s being maintained by ICANN. The difference on Handshake is, anybody can run a Handshake node or operate as a miner, and thus anyone can become an ICANN-equivalent authority over this critical internet component. Because of this, a decentralized DNS layer of the internet can become democratized—it’s become a version of the web that is owned and operated by the People.
Handshake can be thought of as a purpose-built and purpose-designed naming system built in the spirit of Unix philosophy: DOTADIW (Do One Thing and Do It Well). It was built for one thing and one thing only: to replace the ICANN root zone. The "system" being referred to here is not just about (1) the software or the network, but a triad that includes (2) the cryptoeconomic design and (3) the community. While (1) can be easily forked or made obsolete, (2) and (3) are singular, non-repeatable experiments—the defensible moat that surrounds Handshake.
If you’re not convinced, come back in 5 years and reread this post.
Handshake places greater control into the hands of the people who participate in its emerging economy because it is trust-minimized, unstoppable, and incoercible. While it doesn’t implement any explicit governance system in its protocol, its nuanced system of checks and balances echoes that of Bitcoin’s in form, function, and resiliency against Byzantine attackers. This return to the gold standard of a trust-minimized security model is not only paramount, but critical, for the application of decentralized domain names. DNS, as you’ve read, is a foundational networking layer which underpins the Internet itself. In order for a decentralized DNS layer to be truly uncensorable, it must be as resilient as Bitcoin against attempts at capture by the highest levels of power: state-level actors. Knowing this, only Handshake is robust enough to stand up against this threat model.
With this as our guiding thesis, the Decentralized Web (dWeb) Foundation was instantiated to usher in the start of a truly uncensorable, unstoppable Internet—with Handshake at the root.
ABOUT DWEB FOUNDATION
The dWeb Foundation is a wholly community-organized foundation that operates out of Singapore. We are supporters of the early decentralized internet aiming to enable integrations, secondary and tertiary layer infrastructure, and the new generation of internet pioneers to join us in charting the frontier of the third era of the internet.
Handshake is the most secure and only decentralized naming system that offers transparent compatibility with existing DNS infrastructure. The technology seamlessly integrates with the needs of all service providers that offer solutions on top of domain names, making it the ideal base layer for applications like uncensorable social networking, self-sovereign identities, single sign-on with top-level domains, and much, much more.